Tiered SOC structure is something of the past.
The common models of a SOC operation usually looks something like the examples below:

OR

OR

Tiered SOC structure is very ineffective for a few reasons:

- Relying on the least experienced analysts for protection
- Tier 1 analysts are often new hires and:
- Unfamiliar with the environment that they are trying to protect
- Lack of understanding of the threat landscape
- The understanding of an alert logic also plays an important role in triaging
- Analysts need to understand the alert and the environment inside out to make appropriate judgements
- Tier 1 analysts are often new hires and:
- High turnover rate – Tier 1 analysts get burned out the most quickly
- Lack of empowerment – Lower tiers don’t usually get the chance to work on something more meaningful and fun
- Alert fatigue because of triaging similar types of events for a long period of time
- An uneven and sometimes unfair distribution of workloads
So, how do we alleviate some of the issues above?
A more effective SOC model
In this model, we allocate SOC resources based on capacity and specializations.
The analysis & alert triaging workloads are now distributed evenly among the SOC team members but at a capacity of 30%-50%. What do they do with the other 50%-70% of their capacity?
SOC member now can either develop into different specializations of interests (or this could happen during the hiring process too). For example:
- Threat Hunting
- Purple Teaming
- Alert Development
- Data Management
- Threat Intels Management
- Incident Response

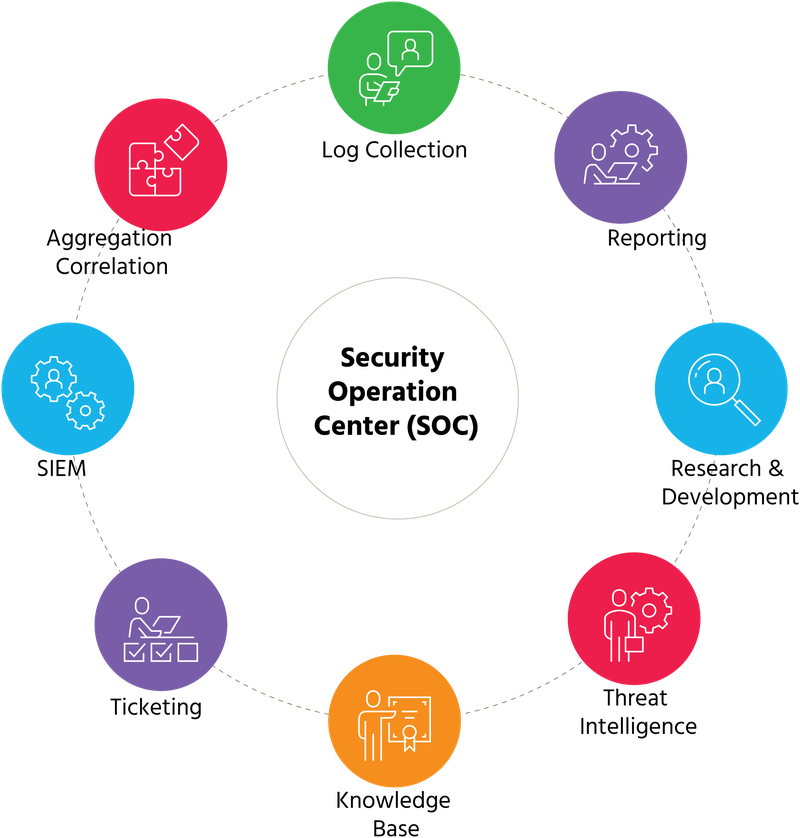
All of these functions create a cohesive SOC system that feeds to each other and collaboratively enhance effectiveness as below:

Now, let’s review what issues mentioned earlier that we could potentially have helped alleviate

Closing thoughts
Having worked in many SOCs wearing multiple hats, from an analyst to an engineer to leading multiple SOC practices (purple teaming, threat hunting, log management, SIEM engineering, alert development, compliance, incident response), this model has proven to yield tremendous valuable results because it’s designed with people in mind.
I know that nothing is perfect but one of the reason that I really embrace this model is that I have always cared about my SOC members, they should be treated evenly, not simply by their tiers.
This model helps show the appreciation and that we want to empower our team members.
Also please not that this model by no mean tries to negate the acknowledgement of levels of seniority and experience within the organization. They can still be applied along with this model in harmony. For example, a more experience threat hunter should still have a higher title and and compensation package than the less experience threat hunter.
Please let me know your thoughts, happy to discuss further.